Hacking
29 posts
hardware
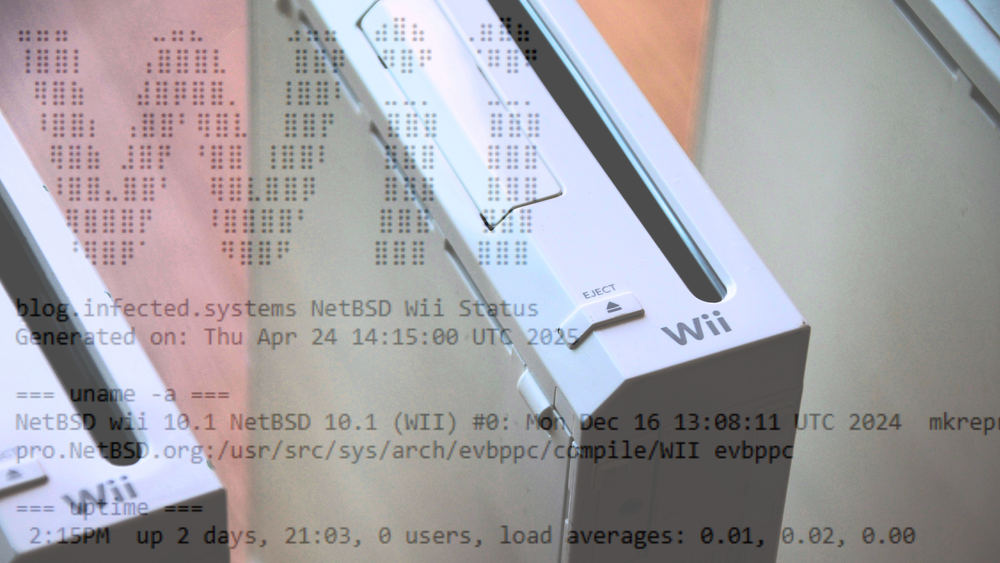
This Website Is Running on a Wii
Alex Haydock found a dusty old Wii console at a hardware swap and modded it to run his website.

News
Beverly Hills Plastic Surgeon Sued for Not Telling Patients Hackers Stole Their Nude Photos
A class-action lawsuit filed against the surgeon claims he also did nothing to protect his patients’ data, including their financial information and nude photos of them.

News
Hackers Mined AT&T Breach for Data on Trump's Family, Kamala Harris
Hackers behind the breach of “nearly all” of AT&T customers’ metadata searched for records associated with members of the Trump family, Kamala Harris, and Marco Rubio’s wife.

News
Hacker Broke into ‘Path of Exile 2’ Admin Account, Hijacked Wave of Characters
The forums for Path of Exile 2 have been awash with people claiming they’ve been hacked and their inventories emptied of valuable items. Now there’s an explanation for at least dozens of the account compromises.
News
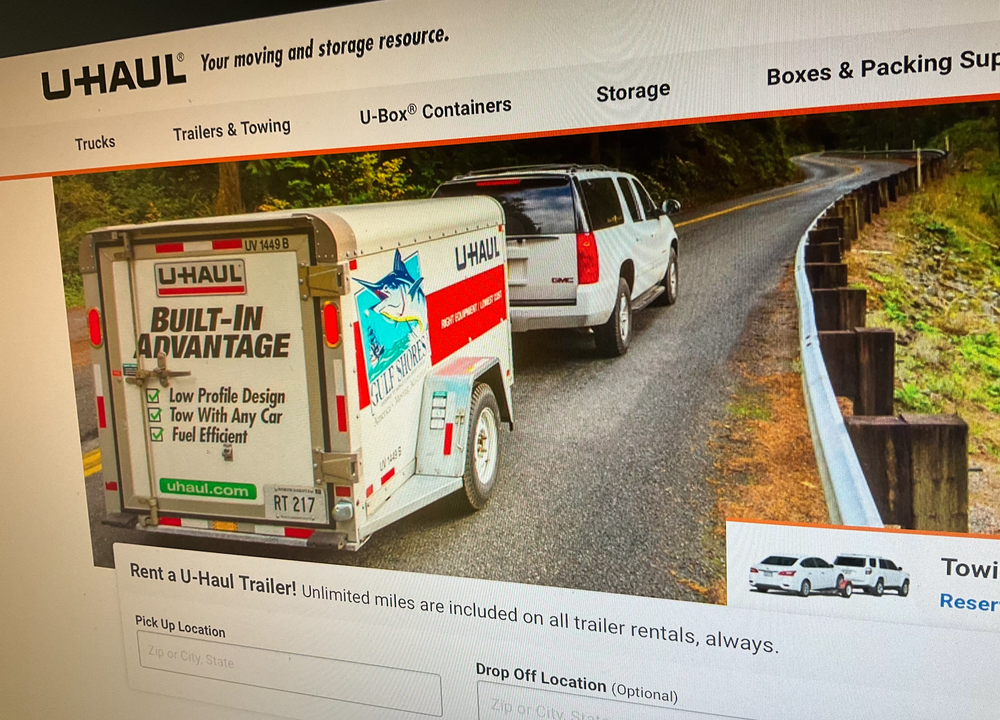
Violent Hackers Are Using U-Haul To Dox Targets
Members of an underground criminal community are targeting U-Haul because of the wealth of non-public information it can hold on targets.

News
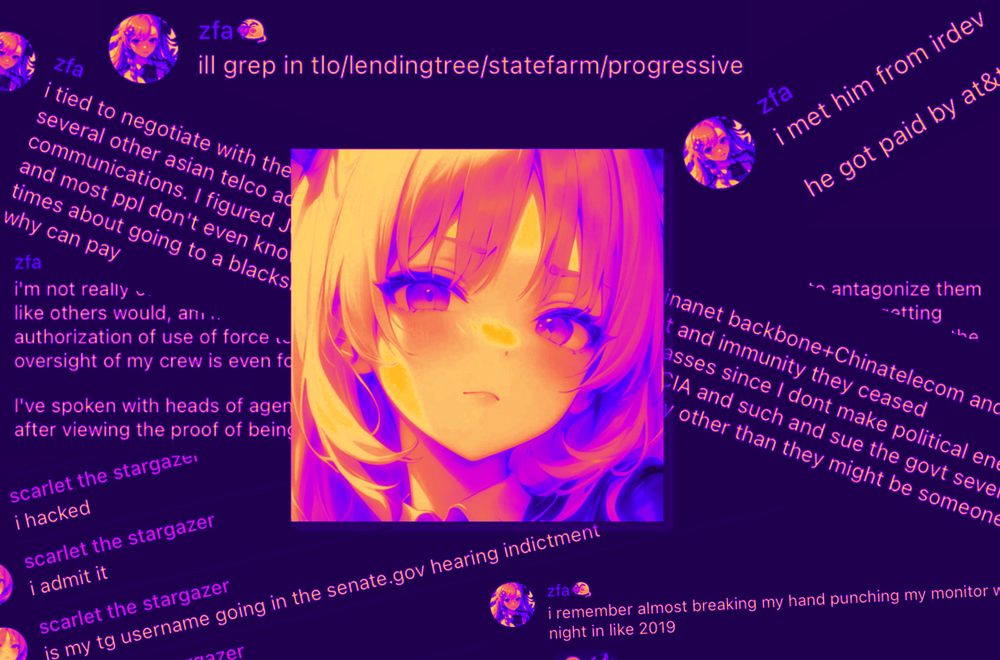
Here’s the Indictment Against the Alleged Snowflake and AT&T Hacker
The indictment also charges a second hacker that 404 Media previously reported as being linked to the AT&T breach.
News
Alleged Snowflake Hacker Appears in Court, Says Prison in Lockdown
Connor Moucka said he didn't have a lawyer yet. He was arrested at the request of the U.S.
News
Suspected Snowflake Hacker Arrested in Canada
For more than a week Judische, the hacker linked to the AT&T, Ticketmaster and other breaches, has not been responding to messages. That's because he's been arrested.

News
Hackers Advertise Stolen Verizon Push-to-Talk ‘Call Logs’
The breach does not appear to impact the main consumer Verizon network, and instead involves the company’s push to talk (PTT) product, marketed to public sector agencies and enterprises.
News
A Network of AI ‘Nudify’ Sites Are a Front for Notorious Russian Hackers
Fin7 has made multiple ‘nudify’ sites that promise to use AI to undress photos of people but which are actually vehicles for malware, according to researchers. 404 Media found one advertised on one of the web's biggest porn aggregators.

News
Ghost, Encrypted Phone for Criminals, Was an ‘Absolute Mess’
A security researcher managed to pull a list of Ghost users, resellers, and even customer support messages from an exposed server. It shows how as organized criminals move to making their own encrypted platforms, they might make vulnerable products.
Features
The Walls Are Closing in on the Snowflake Hacker
As security researchers circle around Judische, and authorities takedown his servers, how much longer will a hacker responsible for breaching Ticketmaster, AT&T, and many more companies remain free?


